Payment card information (PCI) processed by a business’ call center must address several key areas to meet PCI compliance: identifying PCI in the call center environments, implementing PCI DSS compliance requirements, and outsourcing versus not outsourcing.
If a business chooses to retain its call center function, all applicable requirements of the current PCI DSS at the point when compliance is assessed or validated for the call center must be implemented and working effectively. The point-in-time validation does not exclude the business’s responsibility to perform continuous control monitoring for PCI DSS security controls.
This article breaks down the critical aspects of PCI compliance for call centers in detail, and offers recommendations on key issues for companies processing payment cards through this channel.
- What is Payment Card Industry Data in Call Centers?
- What are the PCI Compliance Requirements for Call Centers?
- Top Call Center Risk Factors
- How to Reduce PCI Scope for Call Centers
- Outsourcing to Reduce PCI Scope for Call Centers
- Cost of Call Center Outsourcing
- Other Tactics for Effective Call Center PCI Compliance
- Find the Right PCI Consultant Fast
What is Payment Card Industry Data in Call Centers?
Payment Card Industry Data in a call center is cardholder data and sensitive authentication data (SAD). It can be summarized as follows:
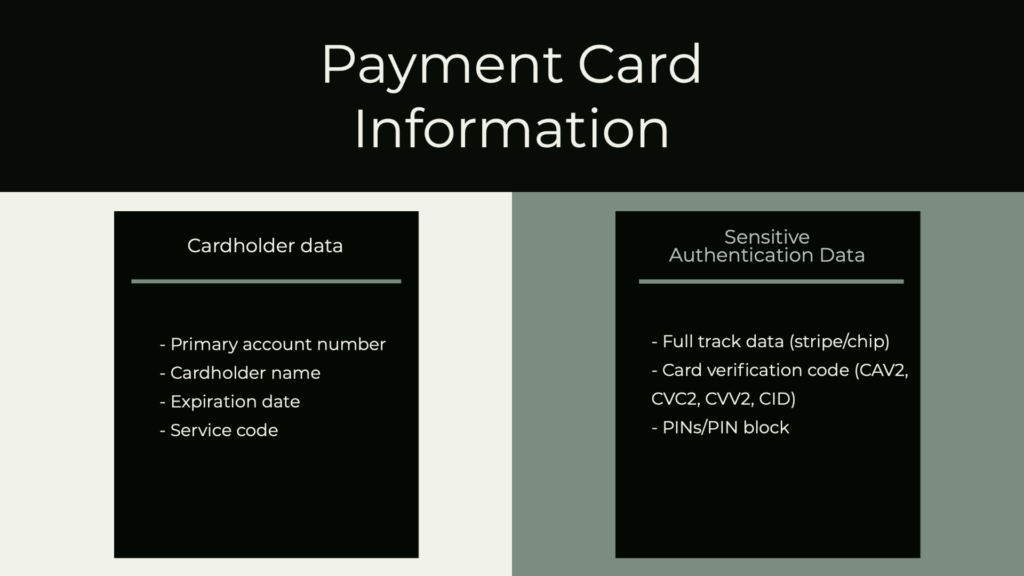
What are the PCI Compliance Requirements for Call Centers?
PCI DSS applies to all system components included in or connected to the call center’s cardholder data environment (CDE). The CDE comprises people, processes, and technologies used in credit card or payment card transactions. The complexity of the telephone environment determines the PCI DSS requirements for implementation.
Outsourcing all or part of the payment card transaction processes to a third party (e.g., Platform as a Service, Infrastructure as a Service, Software as a Service, Data Protection as a Service, or Payment Gateways) can significantly reduce the PCI scope and requirements.
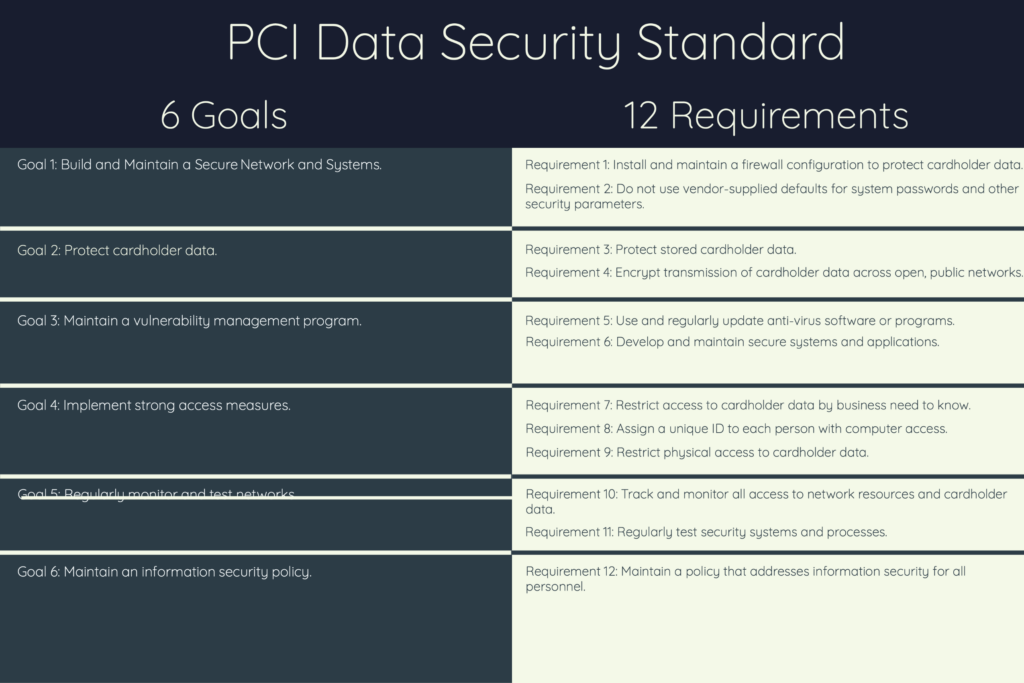
The full set of PCI compliance requirements for call centers are as follows:
PCI DSS Requirement 1: Install and maintain a firewall configuration to protect cardholder data. The business must establish firewall and router configuration standards to manage its networks and systems. Network connections and changes to firewall and router configurations must follow a formal testing and approval process before putting into the production environment. This requirement is in scope if the business manages its own call center. It means the business must:
- Develop, if not already in existence, a network diagram identifying all connections between the CDE and other company networks, including wireless network(s);
- Develop, if not already in existence, a diagram showing all cardholder data flows across the networks and systems;
- Firewalls are installed at each internet connection and between any demilitarized zone and the internal network zone;
- Restrict the inbound and outbound traffic to just what is necessary for the CDE and deny all other traffic;
- Do not allow unauthorized outbound traffic from the CDE to the internet.
PCI DSS Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters at the call center.
- Always change vendor-supplied defaults and keep only the necessary default accounts (e.g., system admin account) before installing a system on the call center network;
- Encrypt all non-console administrative access;
- Implement a policy that addresses the management of vendor defaults and other security parameters – make sure all affected personnel read and acknowledge the policy;
- Remove unnecessary scripts, drivers, features, file systems, and web servers.
(NOTE: Looking for expert advice on your own call center’s PCI compliance? Our free tool below matches your firm with top-rated PCI consultants that suit your needs and budget.)
PCI DSS Requirement 3: Protect stored cardholder data. This means sensitive customer information is encrypted, recording systems disabled (unless needed), and credit card numbers are never in clear text (i.e., mask or hash data). Other controls which help meet this requirement are:
- Only keep what is minimally necessary for business needs;
- Ensure controls are in place to make data unreadable and inaccessible;
- Only personnel with legitimate business needs can access it;
- Immediately delete stored data when it is no longer needed (formal data retention policies);
- Do not store SAD after authorization (even if encrypted);
- Render all data unrecoverable upon completion of the authorization process.
PCI DSS Requirement 4: Encrypt transmission of cardholder data across open, public networks. The open public network (e.g., internet, wireless technologies, cellular technologies, Bluetooth) must use:
- Strong cryptography;
- Trusted keys and certificates;
- Processes for managing encryption are documented and understood by all personnel.
Note: Best practice for PCI compliance at call centers includes implementing and enforcing strict policies prohibiting sending unprotected PANs by end-user messaging technologies (e.g., email, instant messaging, SMS, or chat).
PCI DSS Requirement 5: Use and regularly update antivirus software or programs used throughout the call center. Specifically:
- Identify systems commonly affected by malicious software;
- Deploy antivirus software to these systems;
- For less widely affected systems, perform periodic reviews of the systems against current malware threats to ensure the installation of antivirus software;
- Keep the software up to date.
PCI DSS Requirement 6: Develop and maintain secure systems and applications at the call center:
- Establish a formal process to identify security vulnerabilities within the call center;
- Ensure all vendor-supplied security patches are tested and installed before applications go live;
- Remove development or test accounts, user IDs, and passwords as part of go-live procedures;
- Establish a formal change process and record all changes.
PCI DSS Requirement 7: Restrict access to cardholder data by business need to know. For example, call agents, representatives, and management should only see the minimum account data needed to do their job.
- Define access needs for each role and ensure the following is included:
- System components and data resources needed by each role for their job function;
- Level of privilege required (e.g., user, administrator) for accessing data resources.
- Restrict access to privileged user IDs to only those users who need it to perform their job duties;
- Access is based on the individual’s job classification and function;
- Configure default system and network settings to “deny all.
PCI DSS Requirement 8: Assign a unique ID to each person with computer access.
- Logical access systems should not allow the creation of duplicate user IDs;
- Personnel with access to the call center environment must be controlled, preferably with role-based security;
- Immediately revoke access for terminated users;
- Remove or disable inactive user accounts within 90 days;
- Limit repeated access attempts by locking user IDs out after more than six attempts;
- Require users to re-authenticate terminal sessions after 15 minutes of inactivity.
PCI DSS Requirement 9: Restrict physical access to cardholder data at the call center:
- Limit and monitor physical access to server rooms, data centers, and entry corridors;
- Ensure that all entry/exit points to sensitive areas are controlled and monitored
- Install keycard or biometric scanning technologies;
- Visitors should be approved by a proper company representative and provide picture identification before being given access;
- Visitors are escorted by appropriate company personnel;
- Implement video cameras and access control mechanisms to monitor individual physical access to sensitive areas.
Note: “Sensitive areas” refers to any data center, server room, or area that houses systems that store, process, or transmit cardholder data.
PCI DSS Requirement 10: Track and monitor all access to network resources and cardholder data by implementing audit trails for all CDE system components to reconstruct, for example:
- All individual users who access cardholder data;
- All actions that any individual took with root or administrative privileges;
- Invalid logical access attempts;
- Creation of new accounts and who created them;
- Changes, additions, or deletions of elevated privilege to accounts with root or administrative privileges; and
- Creation and deletion of system-level objects.
PCI DSS Requirement 11: Regularly test security systems and processes, which means:
- Perform penetration testing;
- Ensure intrusion detection and prevention tools are in place; and
- Regularly scan for vulnerabilities and maintain logs of all scans. (See also: Understanding PCI Approved Scanning Vendors)
PCI DSS Requirement 12: Maintain a policy addressing all personnel’s information security.
- Establish, maintain, and communicate a security policy;
- Review the security policy at least annually;
- Update the security policy when the CDE environment changes;
- Develop usage policies defining the proper use of technologies.
Top Call Center Risk Factors

People, processes, and technology are three key risk areas for call centers.
People
People represent the highest risk regarding credit card data security, whether compromises are intentional or accidental. Create and maintain a culture of security within the call center. A policy should be in place to protect credit card data from unauthorized viewing, copying, or scanning.
Do not allow paper and pen or mobile phones at workstations within call centers.
Processes
Companies are required to protect payment cards and sensitive authentication data (PCI Compliance Requirement 3.2). Even if encryption technologies are in place, never store sensitive authentication data after authorization. It is considered a best practice to prohibit recording sensitive authentication data regardless of the complexity of the telephone environment.
Technologies
Ensure all personnel (on-premise, remote, contractors) know that any unauthorized copying, sharing, or storing payment card data is strictly prohibited. Effective monitoring of on-premise and remote workers taking card payments over the phone is vital. Implement strong logical access controls such as:
- Multi-factor authentication when connecting to the telephone environment or to any systems which process account data;
- Restrict physical access to media containing payment card data (e.g., call or screen recordings, USB drives, disable USB drives);
- Only authorized personnel are allowed in business areas with telephone equipment and agent desktops;
- Implement procedures for personnel so they can identify visitors;
- Appropriate personnel must escort all visitors;
- Implement policies requiring remote workers to secure desktops and other telephony; and
- Include the importance of physical security as part of annual security awareness training.
Where account data is input by the call center agent manually typing it, technologies should mask the primary account number; only personnel with a legitimate business reason can see the PAN.
Additional controls to mitigate risk associated with CHD and SAD include:
- Require only company-approved and issued hardware devices;
- Segment the call center into a separate physical area;
- Ensure all desktops have firewalls installed;
- Ensure antivirus software and security patches are up to date;
- Prohibit pen and paper at workstations; and
- Prohibit personal mobile devices at workstations.
Other risks
- VoIP network and the data network lack segregation;
- Ability to record calls;
- Recorded calls are not removed immediately after payment card authorization;
- Workstations are not sufficiently secured;
- Personnel have access to external websites;
- Personnel have download access to files from the web (e.g., pictures, documents, executables), all of which may be corrupted and provide an attacker access to the network;
- Shared accounts due to the high level of call center turnover;
- Lack of clearly defined procedures and policies; and
- Primary account numbers are in clear view, meaning they are not truncated or hashed.
How to Reduce PCI Scope for Call Centers
Dual tone multi-frequency or DTMF
DTMF is the sound you hear when pressing the buttons on a telephone keyboard. When a customer calls and enters their card number by pressing a button, a different tone or frequency is associated with each digit key making it easy for a trained person to recognize a number from the generated tones. DTMF suppression removes or masks these tones by replacing them with a random or flat one.
NOTE: To reduce scope and PCI obligation further, the business should consider using technology that prevents cardholder data from being recorded at the call center.
Network segmentation
At a high level, adequate network segmentation isolates systems that store, process or transmit cardholder data from those that do not. A variety of methods can achieve network segmentation:
- Properly configured internal network firewalls installed between the CDE and the business network;
- Routers with strong access control lists; and
- Other technologies restrict access to a particular segment of a network.
Note: Even if the CDE is segmented to reduce PCI DSS scope, the business’ penetration testing activities (per PCI DSS Requirement 11.3) must include testing of the segmentation controls to verify they are operational and effective.
Voice over Internet Protocol (VoIP)
VoIP traffic that contains payment card account data is in scope for applicable PCI DSS controls, just as other IP network traffic containing payment card account data would be.
Note: VoIP transmissions originating from an external source and sent to the telephone environment are not considered within the entity’s PCI DSS scope until the traffic reaches the business’ infrastructure.
There are three scenarios for consideration when implementing and using VoIP:
- Internal transmissions: VoIP traffic containing payment card account data is in scope for applicable PCI DSS controls wherever that traffic is stored, processed, or transmitted internally over the business’ network.
- External transmissions to other business entities (business-to-business): If VoIP is used to transmit payment card account data to another business (e.g., a service provider or payment processor), the business systems and networks used for those transmissions are in scope.
- External transmissions to/from cardholders: If VoIP is used to transmit payment card account data between a cardholder and the call center, the systems, and networks used for those transmissions are in scope.
Point-to-point encryption P2PE
Point-to-point encryption (P2PE) can significantly reduce the scope of network components, processes, and people. Payment card data is encrypted as soon as taken by the phone agent—the encrypted data transfers to the payment processor, which decrypts the data using a secure key. Using P2PE helps ensure the business never touches card data.
Secure payment gateways
A payment gateway is the front-end mechanism that collects, transfers, and authorizes the customer information in real-time to the business’s bank, where the transaction is processed. Payment card transactions are encrypted and submitted to the secure banking network for authorization settlement.
Using a payment gateway can help much of the PCI compliance burden because the responsibility for PCI compliance rests with the payment gateway.
Examples of payment gateways are PayPal, Apple Pay, and Google Pay, to name a few. These may prove ideal for smaller businesses that do not have the network and system infrastructure or budget to perform the payment transaction lifecycle.
Outsourcing to Reduce PCI Scope for Call Centers
Outsourcing the call center function can significantly reduce the PCI DSS scope for a business. The third-party provider manages the payment card transaction lifecycle: process, transmit, or store. The provider manages components such as routers, firewalls, databases, physical security, and servers. This means that the business using the 3rd party provider offloads the PCI compliance burden for each of those requirements.
However, when outsourcing the call center function, the business remains responsible for identifying and understanding the services and system components included in the service provider’s PCI DSS assessment scope. Both parties must clearly define and understand their respective responsibilities.
Cost of Call Center Outsourcing
The cost to outsource the business’ call center function varies depending on the location and agreement with the vendor. The following cost examples are per hour per call center agent:
- US and Canada: $20-30
- Western Europe: $40 or more
- Eastern Europe: $12-25
- Australia: $35-55
- Africa and the Middle East: $15-20
- Latin America: $8-20
- Asia: $8-15
- India: $6-10
A business looking to outsource must confirm that a potential call center is PCI compliant through documented evidence. If there is a data breach, the business will be in the news, not the third-party call center!
Other Tactics for Effective Call Center PCI Compliance
PCI DSS Requirement 12 pertains to personnel training and gives prescriptive steps for implementation. At a high level, the business call center should:
- Require security training for all new hires and annual training for all personnel;
- If resources allow, have a pop-up window regarding security on the agents’ desktops – they must accept to proceed with the day’s work;
- Encrypt all CHD and SAD at the beginning, so no data is exposed in clear text, ever;
- Disable all USB ports and disc drives.
Call centers serve a vital function in supporting a business’s customer base. PCI compliance for a business’ call center can require implementing all 12 requirements. Implementing network segmentation, data masking, DTMF technologies, and strong, enforceable policies can strengthen the business’ security posture, thereby reducing the scope and cost of PCI compliance to the business.
For further help with PCI compliance, see our list of top-rated PCI Consultancies here.
Consider also our guide to PCI 4.0 compliance, which may affect your call center compliance.









