If you’ve reached this page you’re likely wondering: how do I provide independent verification and validation of my organization’s security controls? Both HITRUST certification and a SOC 2 assessment are great ways to accomplish that need.
Both accomplish that in completely different ways:
- HITRUST provides a validated assessment report which can result in HITRUST certification.
- SOC 2 provides an independent audit of whether or not a service organization meets applicable trust services criteria, which results in an independent auditor report in the form of the SOC 2.
In this article, I’ll provide some opinions about why you’d choose one over another. As a foundational matter, I’ll highlight: SOC 2 and HITRUST both provide high levels of security control assurance and you can’t really go wrong with either one. Some situations do make one preferable over the other and it’s important to understand why and those situations.
(NOTE: If you’re looking for consulting around which security framework to choose, our free tool below matches your firm with top-rated Cybersecurity compliance consultants that can meet your needs and budget.)
HITRUST vs SOC 2 Comparison Table
Before diving into the details, this table offers a comparison between the two frameworks at a glance.
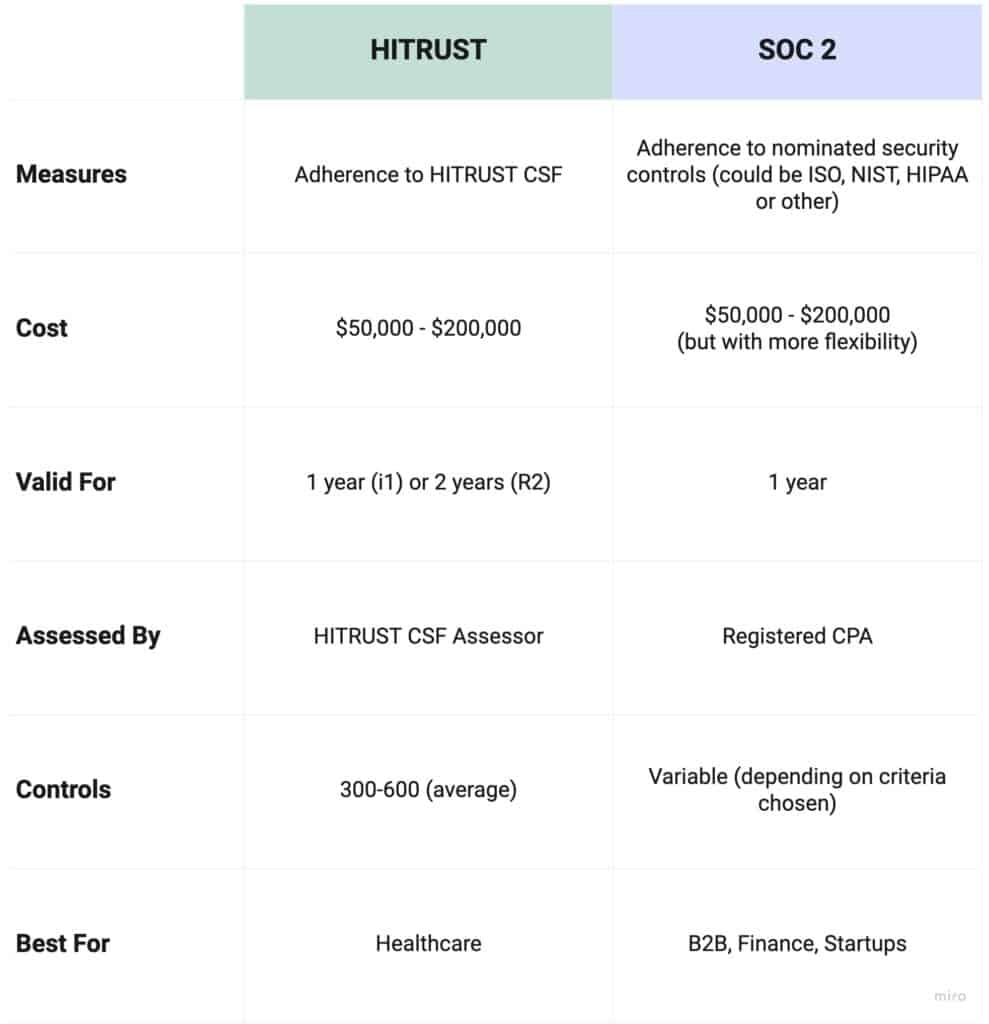
From here, we’ll look at each framework individually, focus on the differences in cost, benefit, and process.
Quick Intro to HITRUST
I’ve covered thoughts about HITRUST at length here and here. The HITRUST Common Security Framework, or HITRUST CSF, was developed by the HITRUST Alliance to meet a critical gap for many in the health care industry and others. Namely, that there was no certifiable set of standards for those organizations to assist with their regulatory compliance needs.
The HITRUST CSF was developed based on industry best practices leveraged from the NIST 800-53, ISO 27001 standards, and various applicable regulatory requirements (like HIPAA). Later, other standards like the NIST Cybersecurity Framework, or NIST CSF, and the MITRE ATT&CK Framework were also included.
Organizations can seek a HITRUST CSF certification after they demonstrate compliance milestones designed to protect sensitive data. An independent assessment vets those compliance milestones and can result in HITRUST certification.
Quick Intro to SOC 2

A SOC 2 assessment is more correctly referred to as an SSAE 18 SOC 2 assessment. The SSAE 18 is the latest iteration of auditing standards promulgated by the American Institute of Certified Public Accountants, or AICPA. The SSAE 18 was developed to, “address concerns over the clarity, length, and complexity of [the Auditing Standards Board’s] standards….“
Those professional standards outline a few different evaluations for service organizations, defined as organizations providing services to client entities, or user organizations, part of those organizations’ information systems. Those evaluations are:
- SOC 1 – evaluates the fairness of a service organization’s management’s description of the service organization’s system and controls regarding financial statements.
- SOC 2 – evaluates management’s description of a service organization’s system and the suitability of its controls with respect to the five trust service criteria: security, availability, processing integrity, confidentiality, and privacy of information.
A SOC 1 assessment focuses on controls over financial processes and is primarily a financial audit opinion, while a SOC 2 assessment focuses on controls over data management processes again, focusing on the trust service principles.
Notably, neither specify a control set against which they should be measured. Instead, they focus on consistent and measurable controls and provide on behalf of service organizations reasonable assurance that they are operating effectively.
Key Differences
The primary difference between SOC 2 and HITRUST is that HITRUST is a certifiable standard based on well-defined controls (the HITRUST CSF framework), while a SOC 2 assessment is a kind of reporting framework that defines the standards to conduct an audit, but not the controls evaluated.
That difference is critical in how each should be approached. A HITRUST certification means that an organization has selected a specific risk management framework around which to build organizational security practices. A SOC 2 assessment means that an organization has hired an external assessor firm to identify whether or not its risk management programs operated effectively over the past year (or evaluated point in time, depending on the SOC 2 assessment type).
As a result, it’s entirely possible to have a SOC 2 HITRUST report if the organization has a SOC 2 conducted for systems adhering to the HITRUST CSF.
Another key difference between SOC 2 and HITRUST assessments is who conducts the assessment. For a SOC 2 report to be recognized, it must be conducted by a CPA firm (or individual CPA assessor) licensed by the AICPA. For a HITRUST-validated assessment to be valid and result in HITRUST CSF certification, the assessor must be qualified by the HITRUST Alliance.
SOC 2 and HITRUST assessments may also have different costs. A SOC 2 assessment must be conducted by an external CPA firm. A HITRUST assessment may be conducted internally if not seeking a HITRUST CSF certification report. However, the HITRUST MyCSF platform does come with a license fee and is required to make HITRUST representations even if not formally assessed.
I think it’s safe to say that both SOC 2 and HITRUST reviews generally cost between $50,000 and $250,000, though there will obviously be significant differences based on scope and the effort involved in conducting the assessments.
How Are They Assessed?
SOC 2 assessments are conducted on a target service organization to evaluate applicable trust service criteria. The focus of that assessment can be on infrastructure, software, staff, processes, and data used to provide services for user organizations.
As highlighted above, a registered CPA will audit a service organization by ensuring the organization answers specific organizational controls on a broad range of security practices. If those security practices satisfy applicable trust service criteria, then a SOC 2 report is issued highlighting areas of compliance and areas of significant risk with respect to the trust services criteria.
There are two types of SOC 2 assessments:
- Type 1 – measures organization controls efficacy for a specific point in time.
- Type 2 – measures organization controls efficacy over an entire year.
The SOC 2 attestation report, whether Type 1 or 2, is effective for one year. Interim assessments can be performed if an organization won’t be reassessed by the end of that year. A bridge letter is issued highlighting that the assessment is ongoing and controls aren’t anticipated to have materially degraded.
A SOC 2 report provides reasonable assurance that an information security program exists and that factors which can bring significant risk to an organization’s operations are being addressed.
The SOC 2 report doesn’t necessarily demonstrate the quality of those controls and instead just provides an attestation report that the controls were validated and an information security program exists. However, the SOC 2 report will outline control deficiencies and requires the implementation of a remediation plan.
A HITRUST assessment generally happens when an external assessor performs an evaluation of an organization’s implementation of the HITRUST CSF common criteria applicable to that organization.
The HITRUST CSF assessor will evaluate a broad range of controls: 219 for an i1 assessment and potentially up to 2000 for an r2 assessment. In a way, certification is dependent on how an organization scores on the HITRUST-validated assessment report. A HITRUST CSF certification report issued for an organization means that an organization meets or demonstrates sufficient progress in implementing the HITRUST framework.
In that way, the HITRUST certification reports do demonstrate quality and quantity of implementation of the HITRUST CSF requirements.
A HITRUST assessment can be valid for one year (the i1) or two years (the r2). Organizations may conduct an interim assessment if they are unable to complete an i1 or r2 assessment within the required timelines.
Both SOC 2 and HITRUST reports are considered confidential to the organization for which they are prepared. Organizations can share their SOC 2 report, or they can have a SOC 3 report generated which omits sensitive nonpublic information from the report. Since the HITRUST assessment is a measure of quality itself based on uniform description criteria, the certification conveys relevant compliance.
Comparing the Benefits of HITRUST vs SOC 2
As I stated in the introduction, I think there are many benefits from both a SOC 2 and a HITRUST assessment. Both assessments are generally accepted risk management tools that provide a verifiable degree of risk management.
The SOC 2 provides more of a “custom assessment” in the sense that whatever security program is implemented by a service organization is evaluated and measured against whatever description criteria exist as a baseline for that program.
Additionally, the validation of trust service criteria is critical for many organizations. By evaluating security, availability, processing integrity, confidentiality, and privacy managed by the service organization’s security practices, the SOC 2 report can serve as a great way to build confidence in organizational controls.
A HITRUST report does largely the same. By assessing an organization’s HITRUST CSF assurance program against well-defined HITRUST assessment requirement statements, HITRUST certification can demonstrate compliance and the quality of the organizational security program.
Both the HITRUST and SOC 2 assessments are assertion-based examination engagements that leverage supporting evidence. That means that an organization responds narratively to predefined description criteria. The auditors or assessors under both then request supporting information to verify and validate controls.
Comparing The Costs
The costs for a SOC 2 and HITRUST report vary. As I highlighted above, I think it’s fair to assume that the general range of costs for most businesses seeking one of these two reports will be between $50,000 and $250,000.
For HITRUST costs, an organization needs to consider licensing fees and assessment fees for the i1 or r2 control sets. Remember, the i1 control set is a static 219 controls evaluated. The r2 can vary from around 200-2000, though are typically in the 300-600 range depending on institutional size, data processed or leveraged, and other factors.
A SOC 2 assessment is more straightforward: an organization will get a Type 1 measuring a single point in time or a Type 2 measuring performance over a year. That being said, some security control frameworks are more complicated than others. For example, a SOC 2 HITRUST report (which is a possibility, as highlighted above) could be an extremely expensive proposition. However, a SOC 2 HITRUST CSF evaluation could provide substantial benefits for different reporting needs.
Who is Each Certification Right For?
HITRUST certification is ideal for healthcare organizations or organizations that are involved in processing electronic health information or health-related records. HITRUST originated as a certification program for healthcare organizations and continues to be well respected in the healthcare industry.
SOC 2 reports are ideal for financial institutions, which are service organizations to many user organizations and likely already produce a SOC 1 report annually. SOC 2 reports are also great for non-financial institutions that require independent audits, whether that’s due to securities law compliance, other regulatory compliance, or because they want to signal to clients that their security program was independently audited. They may also be better for smaller organizations that can’t afford a HITRUST r2 assessment and want that independent evaluation.
If you’re not set on one path or another, you may want to start with a HITRUST bC assessment. Those can be conducted internally and don’t strictly require the HITRUST MyCSF licensing (though it does for representing validation of the evaluation). Unfortunately, the HITRUST bC assessment is being deprecated in favor of a validated e1 assessment and the costs for that are currently unknown.
I’ve previously highlighted that if you’ve decided on a HITRUST i1 assessment as a destination for your organization, you might want to think about a SOC 2 assessment. If you insisted on the HITRUST angle, you could even get a SOC 2 HITRUST controls-based audit report. For your money, I think the SOC 2 Type 1 assessment might be a more effective use of your resources.
That being said, organizations typically don’t stop at the HITRUST i1 and typically progress to the HITRUST r2. I don’t think there’s a more in-depth certification that’s as widely recognized and respected and also generally available. While that might be cost-prohibitive for small and mid-sized organizations, I personally think it’s a good investment to highlight the quality of security controls and signal the seriousness with which your organization takes client data protection.
Conclusion
There are numerous considerations that play into the decision of whether to pursue a SOC 2 audit and report or HITRUST certification. The good news is that you really can’t go wrong here. Both are well-respected institutional assessments and provide a high level of assurance in security programs and data protection. In my mind, it really boils down to whether you want to seek HITRUST certification for your organization or not.









