Ransomware attacks are increasingly common. Companies’ responses to ransomware attacks are anything but.
Of course, when it comes to “handling” ransomware, prevention is better than cure. But when the time for prevention has passed and a company is in the midst of an attack, a different, and very careful approach must be taken.
This guide outlines steps for how companies should handle ransomware from different points in an attack. It also looks at historical examples of what other companies have done during high-profile attacks, to help provide context for the options available.
The goal of the article is to help companies integrate these steps into existing security processes, future threat modeling exercises, and ransomware preparedness plans.
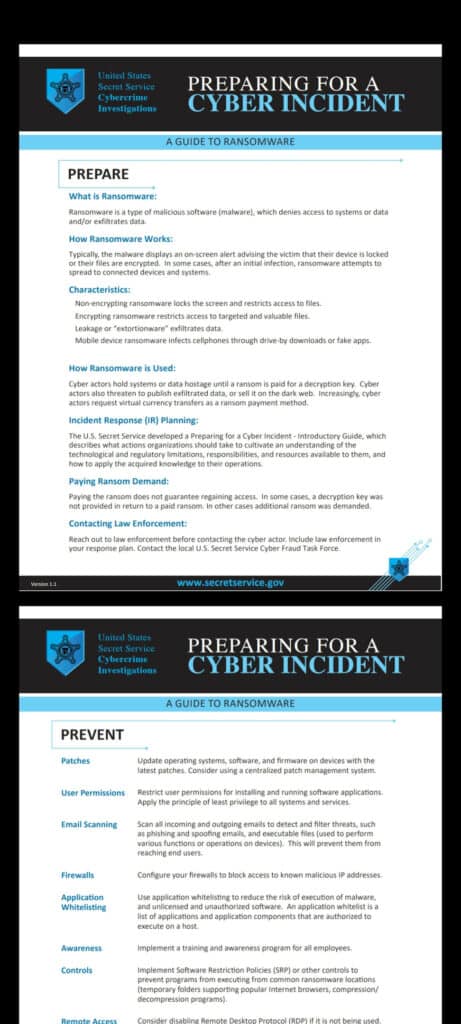
Handling Ransomware Attacks: The Process
The best way a company should handle ransomware and prevent future attacks is to have the mindset of “Defense Wins Championships” and “Practice Makes Perfect”.
Ransomware attacks should be threat modeled in a “war room” type environment, going over the risks within the organization if ransomware was deployed, treating it like an emergency situation.
There is no one-size-fits-all answer to how an attack should be handled. The best response depends on the specific circumstances of each case, however, some general steps that companies can follow when dealing with ransomware include the following:
- Discover patient zero and the infected devices immediately, isolating them from the networks. Remove Ethernet, shut down cloud tunnels, and close network bridges (sandbox). Turn them off if you have to (but remember forensics and clearing memory.)
- Triage impacted systems for system recovery and backups. Critical systems would have primary downtime and loss of revenue especially if these machines are classified as having PII within them for your organization SOC to monitor fully for data exfiltration.
- Keep monitoring with your SOC any breached passwords (HaveIBeenPwned) or abnormal user behavior/logins, data transmission via services like ssh, telnet, tor, SSL, FTP, sftp, etc., since your corporate SIEM and threat intelligence can capture internal lateral movement.
- Monitor web content filtering for chat messaging systems like slack, telegram, Whatsapp, Gmail, protonmail, etc., in making external connections part of data exfiltration. Also, monitor for temporary browser email servers like guerilla mail.
- Keep documenting and collecting evidence as you enact your incidence response plan as necessary throughout the attack based on outages and data compromise. This will be used for forensics in upcoming legal counsel meetings, or FBI/Gov debriefs.
- Enhance your Information Security Program with updated policies and procedures with missing learned techniques based on the information teams are learning from the ransomware attack.
- Reconfigure the technological holes in how patient zero got compromised and how the ransomware attacked the organization, whether lateral movement, file share-seeking data encryption, data exfiltration, user compromise, or virtual environment takeover. How did the attack evolve?
- Contact your internal and external stakeholders per your information security plans, policies, and procedures for help with those impacted during the breach, whether customers, your legal counsel or the forensics company.
- The local/ Internet authorities have resources for potential decryption keys and knowledge of IOCs for discovering Ransomware and other resources like attacker I.P.s to help with firewall I.P. lists to help with isolation.
- If your company got sideswiped by not having proper backups or loss of critical infrastructure, DO NOT PAY RANSOM until federal resources have been researched for decryption keys or evidence that the ransomware group even decrypts files after payment.Also, research if paying the ransom is even Legal, as in some situations paying a ransom could be illegal.
- Revert all knowledge of proactive assessments in determining how the attackers breached the organization through external reviews, web application assessments, social engineering, password strength, and third-party application breaches in knowing where attackers can compromise your risk with ransomware attacks. If you pay the ransom, the company needs to make sure the attackers can’t just deploy the ransomware attack again, which is why the root cause needs to be determined from forensics.
- Keep in mind forensics throughout this process is preserving evidence during the attack, which can be passed along to law enforcement and determining vulnerability in how the organization was attacked. I.P.s, server-side logs, network traffic, external connections, I.P. tables, changed registry files, dropper files, malicious scripts, malicious hos processes and ports, memory logs, firewall activity, DLP, or Content filtering activity.
- Monitor data breach dark web platforms to see if any sensitive data that was a part of the enterprise networks hasn’t been posted to these forums. Senior Leaders should consider if they will pay the ransom on these dark web forums after a successful attack to ensure that any victim’s data or affected parties are known and adequately handled.
How Not to Handle Ransomware Attacks
From the hundreds of assessments I’ve conducted against organizations of all sizes, industries, and configurations, the worst way to handle ransomware attacks is to be reactive to the entire situation.
Every company knows ransomware attacks happen, attacking bad user passwords, misconfigured services, poorly managed regular backups, or outdated software. From conducting hundreds of interviews with Chief Information Security Officers, Compliance Officers, legal counsel, Engineers, and other departments (HR, Finance, Marketing), individuals are usually just overwhelmed with the security industry that they get overloaded instead of solving the root causes of these risks.
Suffering from complacency and lack of security knowledge or without taking the mindset of a “what would a potential hacker do,” companies usually choose to:
- Not conducting penetration testing against external or internal environments to determine risks.
- Not social engineering your employees via vishing, phishing, or spear-phishing to see where your email and anomalous user behavior detection mechanisms are lacking.
- Not threat model war room situations like Ransomware or DDoS combined with a mock breach to ensure, when under pressure, individuals understand the processes of catching the advisory, protecting confidential information, and bringing justice with forensic evidence.
- Not running vulnerability assessments against workstations, BYOD, Servers, Networking devices, or the Internet of things (IoT).
- Not conducting Web Application Risk assessments with OWASP Top 10 methodologies against your databases or Cloud Environments or train DevSecOps on how to set up Software Development LifeCycle for developers to secure code.
- Not testing the backup schedule of your critical infrastructure or customer information. While never tested to see if your company can redeploy the domain controller within your virtual environment after a compromise.
- Not tuning your SIEM, IPS, DLP, SSL inspection, patch management, Web, or Content filtering after it’s been implemented and move into the next project.
How Companies Have Handled Ransomware Attacks

Colonial Pipeline
The Colonial Pipeline was hit with a ransomware attack by the DarkSide gang, targeting the firm’s billing system and internal business network, leading to widespread shortages in multiple states. Due to the impact of gasoline shortages on Americans, Colonial decided to pay the ransom to get their systems back online.
US law enforcement recovered much of the $4.4 million ransom payment. The FBI traced the money by monitoring cryptocurrency movement and digital wallets. But finding the actual hackers behind the attack will prove a lot harder.
JBS Food
The same Russia-based hacking group that attacked Acer, REvil, is thought to be behind the attack against JBS food around the same time as Colonial Pipeline in May 2021. Although there weren’t any significant food shortages due to the attack, government officials told consumers not to panic buy meat in response.
On June 10th, it was confirmed that JSB paid the $11 million ransom demand after consulting with cybersecurity experts. This massive payment in bitcoin is one of the most significant ransomware payments of all time.
KASEYA
REvil, the same hacker group that targeted Acer, Quanta, and JBS Foods, again made headlines in July 2021 with an attack on Kaseya. While not a name commonly known by consumers, Kaseya manages IT infrastructure for major companies worldwide.
According to Kayesa, around 50 of their clients and about 1000 businesses were impacted. The hacker group demanded $70 million in bitcoin. To illustrate the impact of the cyber attack, Coop, a Swedish supermarket chain, was forced to close 800 stores for a whole week. Soon after the attack, the FBI gained access to REvil’s servers and obtained the encryption keys to resolve the hack. Fortunately, no ransom was paid, and Kaseya could restore its clients’ IT infrastructure.
Should Companies Ever Pay the Ransom?

There are many reasons to pay the ransom and not to pay the ransom. Is it legal to pay the ransom? Will they release the decryption keys? Will they just deploy ransomware again after payment? You can learn a lot about the attackers by analyzing how they attacked your company, how they are demanding the ransom, and if they have attacked other victim’s companies simultaneously to see if they are going to release decryption keys.
I have had to communicate with the ransomware support teams via a web chat to get a client’s decryption key. We had to teach my client how to buy Bitcoin to transfer it to the ransomware attacker’s BTC wallets to try to get their files decrypted. We suggested this to the client because their corporate backups were not configured, so they lost multiple companies’ data. Hence, they only had one option: to pay the ransom in hopes that the attacker (who in this case did) provides a working decryption tool, otherwise the companies would have been out of business.
If it’s your last resort, consult forensics, legal, and federal agencies on how to pay a ransom demand to decrypt files. This is so you can get your critical assets and data back in order; however, the root cause of how the attacker compromised specific systems will still be unknown.
When Should Companies Involve Law Enforcement in a Ransomware Attack?
This is a classic question because no company wants to be embarrassed to have to notify stakeholders of a breach. Here are some questions to ask your teams when creating a ransomware attack plan.
- What is your cyber liability insurance requiring you to do?
- What does your legal counsel require for their forensics contract?
- Any compliance or regulatory requirements forcing notification?
- What does your incident response plan state?
If you’ve been monitoring the attack, your report could aid authorities in determining the attacker’s motives. The local InfraGard chapter/ FBI/ police can assist your investigation by gathering information on your attack and developing the claim.
Similarly, you need to notify any of your customers via mail based on the classified PII that was stolen. This can include customers, suppliers, employees, or other companies affected by the ransomware attack, as stated in the company’s incident response plan.
There are a couple of ways of contacting authorities so your company can share the threat intelligence of the ransomware attack appropriately.
Federal asset response
Upon voluntary request, includes providing technical assistance to affected entities to protect their assets, mitigate vulnerabilities, and reduce impacts of cyber incidents while identifying other entities that may be at risk, assessing potential threats to the sector or region, facilitating information sharing and operational coordination, and providing guidance on how to best use federal resources and capabilities.
Federal threat response
Upon voluntary request, includes law enforcement and national security investigative activity: collecting evidence and Intelligence, providing attribution, linking related incidents, identifying additionally affected entities, identifying threat pursuit and disruption opportunities, developing and executing an action to mitigate the immediate threat, and facilitating information sharing and operational coordination with asset response.
CISA:
For more questions on this topic or CISA in general, please get in touch with Central@cisa.gov. To report anomalous cyber activity and cyber incidents 24/7, email report@cisa.gov or (888) 282-0870.
Cybersecurity Advisor:
CISA Regions | CISA: [Enter your local CISA CSA’s phone number and email address.]
MS-ISAC:
soc@msisac.org or (866) 787-4722
FBI and or local InfraGard Chapter:
https://www.fbi.gov/contact-us/field-offices
[Enter your local FBI field office POC phone number and email address.]
USSS:
https://www.secretservice.gov/contact/field-offices
[Enter your local USSS field office POC phone number and email address.]
CiSP
Cyber Security Information Sharing Partnership (CSIP) provides organizations from all over the U.K. with the best possible platform and resources. We encourage member companies to share technical data to reduce the risk of new attacks, particularly Ransomware.
Others:
NCSC operates a commercial program called Cyber Incident Response. Certification firms offer assistance to organizations affected.
Multi-State Information Sharing and Analysis Center (MS-ISAC): https://learn.cisecurity.org/ms-isac-registration
Election Infrastructure Information Sharing and Analysis Center (EI-ISAC): https://learn.cisecurity.org/ei-isac-registration
Sector-based ISACs – National Council of ISACs: (nationalisacs.org)
Information Sharing and Analysis Organization (ISAO) Standards Organization
The U.S. Department of Homeland Security (DHS) and the U.S. Department of Justice (DOJ) established the StopRansomware.gov website to help private, and public organizations access resources to mitigate their ransomware risk. https://www.cisa.gov/stopransomware
Reverse Engineering the Ransomware Threat to Protect your Organization
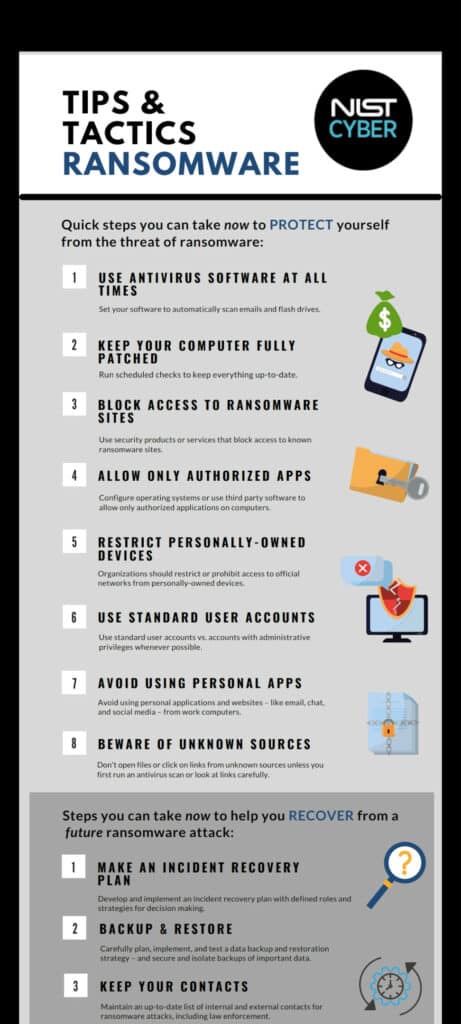
Companies that are serious about security develop specific ransomware preparedness plans (as part of or in addition to a broader incident response plan) to reduce the potential for damage in the case of an attack.
Being prepared means having the technology, employees, and policies in place so that the response to an attack is – to the largest degree possible – predefined, rather than reactive.
As well as pre-attack planning, the organization’s CISO, CCO, DPO, legal counsel, executives, I.T., and security teams should meet regularly on how to remediate specific ransomware situations that could arise. These meetings can aim to clarify and tie together some of the following policies and procedures:
- Incident Response Plan
- Disaster recovery Plan
- Ransomware Response Plan
- Web & Content filtering
- Operating system and third-party patching
- Network architecture and segmentation
- Critical Data classification Plan
- Application Risk Analysis
Remember that any organization can suffer a ransomware attack, but only a prepared organization can survive one.
As a final note, the United States Government also supplies many resources to help companies prepare for ransomware attacks, some of which are listed below: